Ansible is a tool for configuration management, let's dive into the problem and its solution.
Problem
Let's say your organization has an on-premise server that has 100 servers, you have to log into each system and manage the configuration like system updates, security patches and more, and it will be a tedious task if servers were 1000 or 10000.
When Cloud comes into the picture, the number of servers increases by 10 times but size decreases by 10 times as using microservices.
so instead of managing configs of each server manually, tools come into the picture to make it easy for us to manage even 1000 or 10000 servers, tools like -
Ansible
Salt
Chef
Puppet
Solution
Ansible makes it easy by writing configs in a YAML file and config all the servers, you just have to define the IP address of all servers into an inventory file and Ansible will take care of the rest.
You can manage as many machines using Ansible, it supports both Windows and Linux.
Ansible Hands-on workshop
Task: Setup Ansible on one machine and configure another machine using the first one, launch two EC2 instances, on the first one(name this one ansible_server), we set up Ansible and configure the other one(name this one main_server) from this ansible server.
I chose Ubuntu as the OS with a free tier.
SSH into ansible_server EC2 instance
ssh -i <public_key.pem> ubuntu@<public ip>- Update the system
sudo apt update
- Install Ansible using the package manager
sudo apt install ansible
- Verify the installation
ansible --version
- Setup password authentication for Ansible If you normally try to SSH into our main_server from ansible_server it'll require a password each time you log into it.
So, for that set up a passwordless authentication
- Generate SSH keys in ansible_server
ssh-keygen
it'll generate one private key and one public key, never use your private key, always use the public key.
these generated keys are in .ssh directory
- Copy public key
cat <your_keyname>.pub
and copy it.
- Now SSH into main_server from another tab Generate the SSH keys here also and open the authorized_keys file and paste the SSH public key from our ansible_server once you do that you can SSH into main_server from ansible_server,
ssh <private_ip_of main_server>
Ansible
There are many ways to config things using Ansible,
Ansible Adhoc Commands
Ansible Playbooks
Ansible Roles
Ansible Adhoc commands
For simple and minimal tasks, use Ansible Adhoc commands.
Make a directory to store the ansible inventory file, and create an inventory file to store our IP address of EC2
mkdir ansible
cd ansible
vim inventory
In Inventory file
<Private IP of main_server>
and run ansible command to create a file on main_server
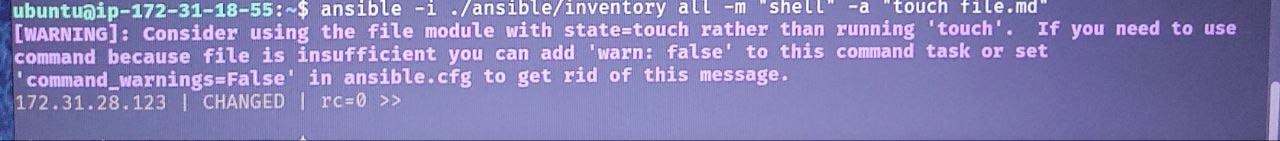
ansible -i <inventory file location> all -m "shell" -a "touch file.txt"
all apply this command to all mentioned IP addresses in the inventory file
-m flag for module and in our case is shell
-a flag for the argument
Ansible Playbook
For complex and large tasks, let's learn it by doing a task.
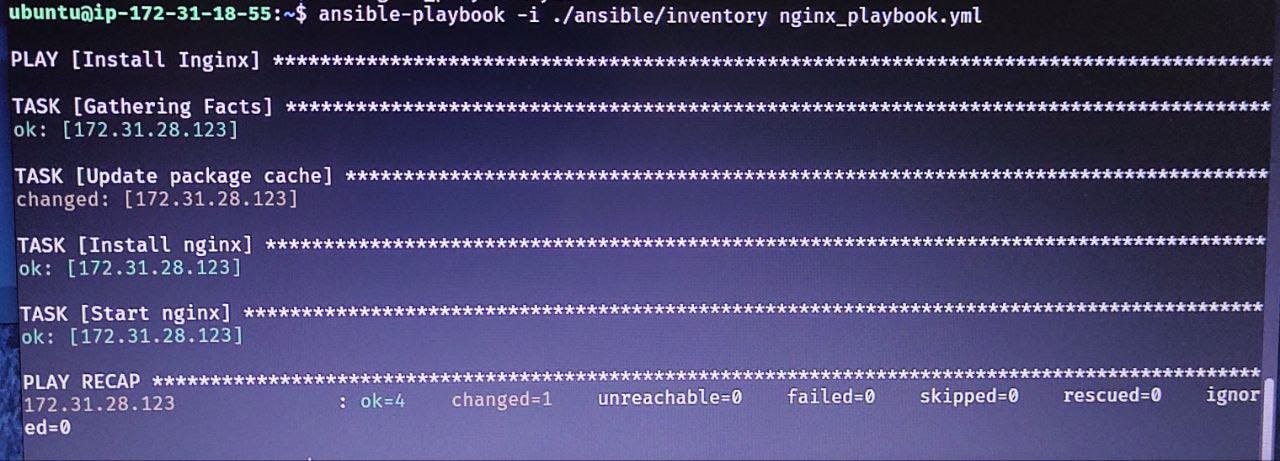
Task: Install and start nginx on main_server using Ansible
- Write a playbook file
vim nginx_playbook.yml
---
- name: Install Inginx
hosts: all # for all IP address
become: true # run tasks as a root user
tasks:
- name: Update package cache
apt:
update_cache: yes
- name: Install nginx
apt: # ubuntu package manager
name: nginx # package name
state: present # to install
- name: Start nginx
service:
name: nginx
state: started
- run this command
ansible-playbook -i <inventory file location> <playbook yml location>
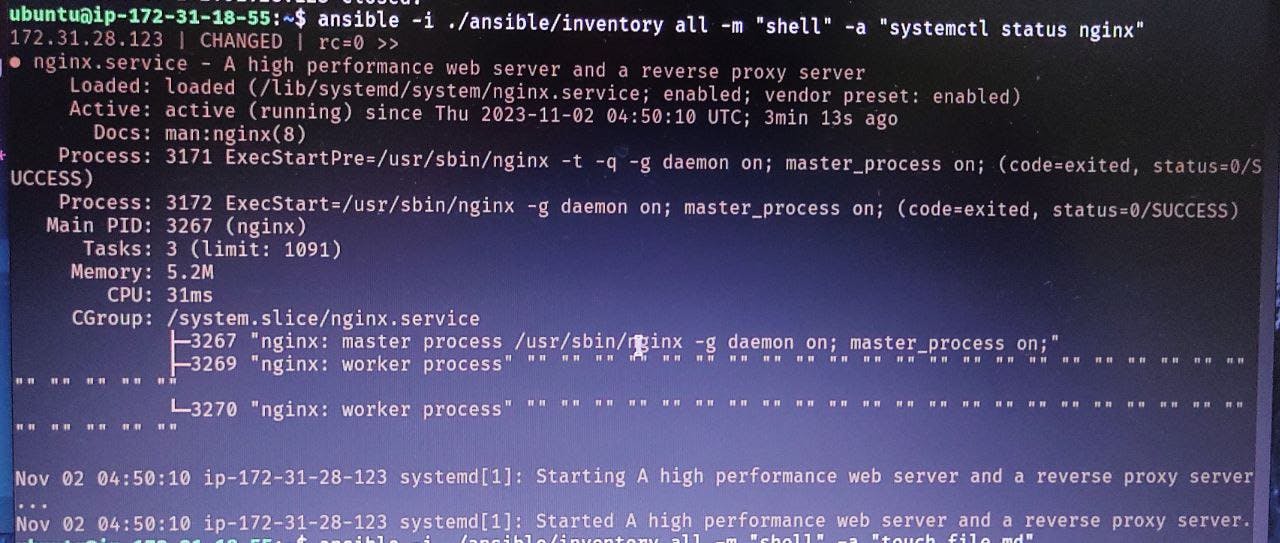
- Check the status of Nginx
Ansible Roles
It is an efficient way to write ansible playbooks
Here are some detailed and practical blogs
Ansible Playbook Role code for configuring Apache - Github Repo